Steps to replicate the issue:
- Load coffeebase.wikibase.dev in a browser
What happens?:
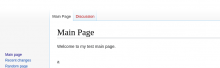
No logo is visible.
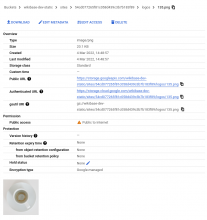
In the network tab we can see:
https://storage.googleapis.com/wikibase-dev-static/sites/54cd077265f81c058d439c3b7b183f89/logos/64.ico is returning a 403 with text
<Error> <Code>AccessDenied</Code> <Message>Access denied.</Message> <Details>Anonymous caller does not have storage.objects.get access to the Google Cloud Storage object. Permission 'storage.objects.get' denied on resource (or it may not exist).</Details> </Error>
What should have happened instead?:
Logo should have been visible
Software version (skip for WMF-hosted wikis like Wikipedia):
wikibase.cloud
Other information (browser name/version, screenshots, etc.):