What is wrong
Window 1
Window 2
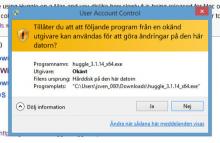
Window 3
There is no publisher (Swedish: Utgivare) designated when installing Huggle. It says Unknown (Swedish: Okänd) This is causing Windows SmartScreen (or whatever it is called) to try to put up a fight when installing this file.
How to fix
- Someone need to purchase a certificate for this purpose from certification authority that is trusted by Microsoft by default (around $600 for 3 years or $1000 (better variant))
- Once the certificate in .pfx format is available to people trusted with Huggle releases and distribution (see https://github.com/orgs/huggle/teams/release-managers) use this guide to sign the .exe files: https://stackoverflow.com/questions/84847/how-do-i-create-a-self-signed-certificate-for-code-signing-on-windows