Currently, the following workflows exist within AuthManager (where a link provider could be involved):
- Special:UserLogin -> authenticate (with external source) -> logged in (the external source user is already linked with a local wiki user)
- Special:CreateAccount -> authenticate (with external source) -> account created
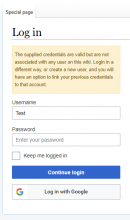
- Special:UserLogin -> authenticate (with external source) -> not logged in (the external source user is not linked with a local wiki user) -> the user has to authenticate with another method, e.g. with Password
However, with the last workflow, the user currently is a bit lost now. He wanted to authenticate with the external source (e.g. Google) and was successfully authenticated. The only problem is, that the user isn't connected with a local wiki user, so as a "normal" user I would expect to get the chance to create one now. But unfortunately, I would need to manually open Special:CreateAccount or go back to Special:UserLogin to click "Create an account". That doesn't look very intuitive. Maybe we could implement a new workflow like:
- Special:UserLogin -> authenticate (with external source) -> not logged in (the external source user is not linked with a local wiki user) -> create a new local wiki account -> logged in
While implementing this, the following use case should be considered, too:
As a wiki administrator, I maybe want to disable "normal" account creations, but want to allow new account registrations with a link provider. E.g. I've a company with Google Apps for business. So my wiki should be visible (and editable) by users with a Google Mail account (with a specific domain), only. For this I want to allow user registrations with a valid Google login, but not a "manual" registration with Username/password.