Block cookies are only added on page load. As many communities use the VisualEditor as the default editor for logged-out users, the block cookie should be added on all users, regardless of editor they use.
Current behavior
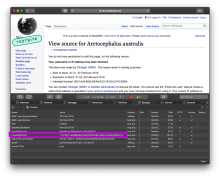
When users edit with the desktop source editor, the block cookie drops:
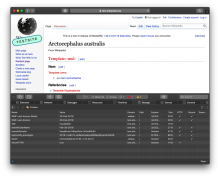
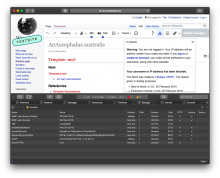
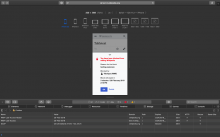
However, they are not dropped with tools that make edits via API, such as the VisualEditor or mobile web editor:
| No block cookie | Still no block cookie when VE opens and "you are blocked" message appears | No block cookie when edit is rejected |
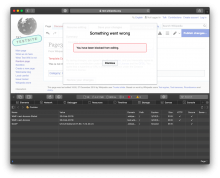
| No cookie when mobile web "you are blocked" message displays |
Acceptance criteria
- Users should receive a block cookie when they attempt to edit with the VisualEditor — when the editor loads and displays the "you are blocked" message
- Users should receive a block cookie when they attempt to edit with the mobile web editor — when the editor loads
- The block cookie logic should behave the same it does in T152462 and T5233
Notes
- We can break these up into as many investigation + implementation tasks as needed.
- Can we piggy-back off the "you are blocked" notice tracking we implemented in T189724 ?