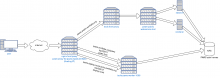
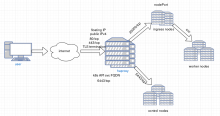
This task is to track the work specifically to figure out paws-public in the modern service model we are introducing for PAWS.
Previous to the new model, it worked like this:
Some comments:
- the paws-public toolforge webservice is creating an ingress with a domain that should be rejected by our custom ingress admission controller, how is that even working?:
tools.paws-public@tools-sgebastion-07:~$ kubectl get ingress NAME HOSTS ADDRESS PORTS AGE paws-public-custom paws-public.wmflabs.org 80 110d paws-public-legacy tools.wmflabs.org 80 110d
- I believe @Bstorm suggested we could simply run nbserve and the renderer in the paws k8s cluster, so we effectively decouple from Toolforge
- in such case, we could introduce a new domain public.paws.wmcloud.org and a legacy redirection from paws-public.wmflabs.org.
- This is required for T160113: Move PAWS nfs onto its own share and T167086 to work as expected if we want paws-public to continue to be updated by user activity. Otherwise it would become an archive.
- The image(s) should be added to the quay.io repo in the end of this so that they are maintainable by all PAWS admins instead of Toolforge admins only.