Hello Wikipedia,
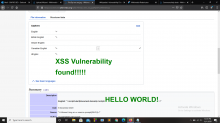
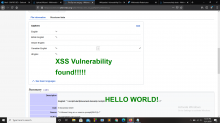
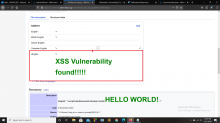
I found a vulnerability on this subdomain of Wikipedia.([[ commons.wikipedia.org | Wikipedia Common ]] ).It is Cross-site scripting (XSS).I already have an account in Wikipedia.Then i go to wikipedia common website.Then i try to upload a picture for test.I upload a picture successfully.In the file information their is a option named Captions.Then i edited my caption as Payloads.And i successfully upload my payloads & found that their is a vulnerability.I attached a screenshot below.
For your kind information my paylaod is "><strong><script>alert(document.domain)</script><font color="green" size=14px>XSS VULNERABILITY FOUND!</font></strong>
By exploiting this bug hackers can steal your website cookie & so on.Please fix it ASAP.