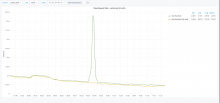
At 09:36 this morning, @elukey noticed a sudden surge in the requests to text-varnish in ulsfo
Looking at the sampled-1000 data, I found ~ 120k requests with the following characteristics:
- All for https://wikipedia.org
- All from IPs from telus.net dynamic ip pools, see https://w.wiki/33T9 (restricted to NDA)
- All followed the redirect to https://www.wikipedia.org
*All with user-agent Mozilla/5.0 (Windows NT 6.1; WOW64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/29.0.1547.66 Safari/537.36
Of note: Chrome 29, according to https://en.wikipedia.org/wiki/Google_Chrome_version_history was released in august 2013.
It looks like some coordinated request, possibly non-malicious, like a connection test from routers. There is a similar spike at around the same time during the Pacific night, between 8 and 9 UTC on January 7th, but I'm not sure if we can still verify what was in those requests.