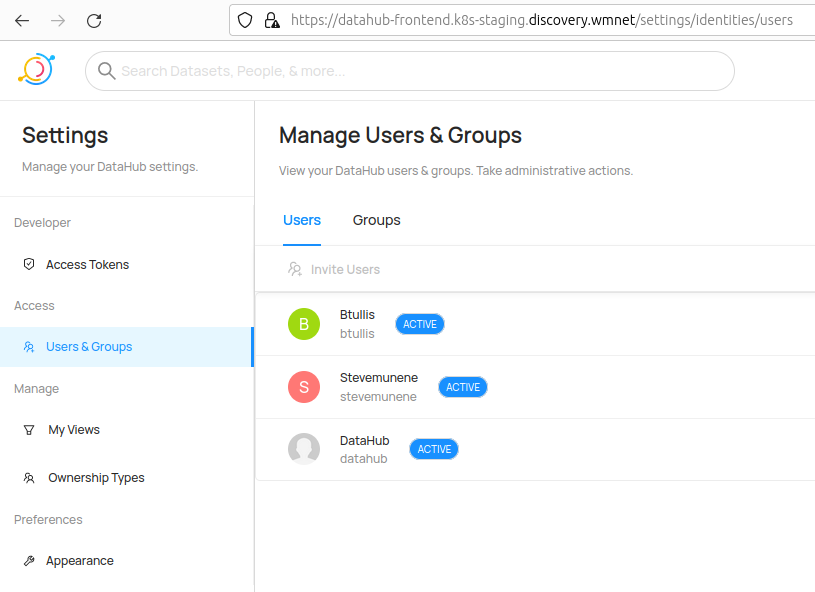
We are aware of an issue with datahub whereby newly logged in users do not appear to be added to the database as user records.
This means that it is impossible to assign elevated rights to the individual, such as adding them to the datahubadmins group.
For example, we know that the users stevemunene and jebe have logged in, but there is no urn for them.
MariaDB [datahub]> select urn,aspect from metadata_aspect_v2 where urn like '%stevemunene%'; Empty set (0.000 sec) MariaDB [datahub]> select urn,aspect from metadata_aspect_v2 where urn like '%jebe%'; Empty set (0.042 sec)
Compare that result to the result for btullis who is already a member of datahubadmins
MariaDB [datahub]> select urn,aspect from metadata_aspect_v2 where urn like '%btullis%'; +-------------------------+-----------------------+ | urn | aspect | +-------------------------+-----------------------+ | urn:li:corpuser:Btullis | corpUserEditableInfo | | urn:li:corpuser:btullis | corpUserInfo | | urn:li:corpuser:btullis | corpUserKey | | urn:li:corpuser:btullis | groupMembership | | urn:li:corpuser:btullis | groupMembership | | urn:li:corpuser:btullis | groupMembership | | urn:li:corpuser:btullis | groupMembership | | urn:li:corpuser:btullis | nativeGroupMembership | | urn:li:corpuser:btullis | nativeGroupMembership | +-------------------------+-----------------------+ 9 rows in set (0.039 sec)
When stevemunene logs in, we can see two specific errors in the log files.
10:30:15 [application-akka.actor.default-dispatcher-82433] ERROR application - The submitted callback is of type: class javax.security.auth.callback.NameCallback : javax.security.auth.callback.NameCallback@619b7182 10:30:15 [application-akka.actor.default-dispatcher-82433] ERROR application - The submitted callback is of type: class javax.security.auth.callback.PasswordCallback : javax.security.auth.callback.PasswordCallback@72e4e2a1
I'm not yet sure what this means.
It's possible that this behaviour started after the upgrade of datahub to version 0.9.0 but we're still correllating these dates.