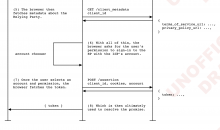
Federated Credential Management (spec, explainer, MDN, platform status, demo) is Google's proposed solution to anti-tracking features breaking federated login on some sites. It's officially in development but has been enabled in Chrome for half a year now, and other vendors seem supportive. We should investigate it as a potential CentralAuth autologin replacement that's better aligned with web trends.
It seems to build on top of the Credential Management API (spec, web.dev, MDN, caniuse, WWCDT) so we should look into that as well.