As the lead developer and security person of the Liquipedia wiki farm, I got a security report about an XSS issue in Extension:PageForms.
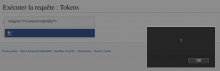
I have put a minified test case on the SemanticMediaWiki sandbox here https://sandbox.semantic-mediawiki.org/wiki/Spécial:RunQuery/Tokens, as this combination with Semantic MediaWiki is how it has been reported to me.
The issue can be seen by posting something like <img/src=="x onerror=alert(1)//"> into the input field, or by going to a url like https://sandbox.semantic-mediawiki.org/wiki/Sp%C3%A9cial:RunQuery/Tokens?title=Sp%C3%A9cial%3ARunQuery%2FTokens&pfRunQueryFormName=Tokens&Tokens+test[capital][]=%3Cimg/src==%22x%20onerror=alert(1)//%22%3E&Tokens+test[capital][is_list]=1&pf_free_text=&wpRunQuery=Run+query which provides the form parameter as a url GET parameter.
This bug has been reported to us by Gilang Romadon
If you need any more information, feel free to message me or post into the bug, I hope the example use-case will help.
Best Regards
Alex Winkler