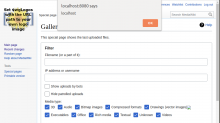
On Special:NewFiles, all the mediastatistics-header-* messages are output in HTML unescaped.
Steps to reproduce:
- Edit one of the mediastatistics-header-*messages (e.g. edit MediaWiki:Mediastatistics-header-drawing) and add a simple XSS string like <img src=x onerror=alert(document.domain)>
- Visit Special:NewFiles and see the JavaScript executed
This happens because the form options is using the ->text() output format with options, which is not escaped, rather than options-messages.
It's relatively low risk given it's admin-only, but filing as a private issue similar to T256171 and T255918.