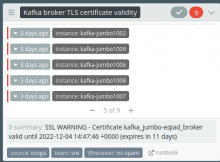
We need to update the certificates for the kafka-jumbo cluster. Our monitoring system has alerted us to their upcoming expiry.
SSL WARNING - Certificate kafka_jumbo-eqiad_broker valid until 2022-12-04 14:47:46 +0000 (expires in 11 days
The process to update the certificates is described here: https://wikitech.wikimedia.org/wiki/Kafka/Administration#Kafka_Certificates
Since we need to take action quickly, I am expediting this ticket into the current #shared-data-infrastrcuture sprint. I will assign the ticket to myself (@BTullis) and carry out the work, with @Stevemunene shadowing.