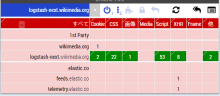
See the picture, kibana next sending telemetry to elastic.co
We are handling sensitive privacy things at kibana.
I guess better to we should disable that.
Solution
- Telemetry settings in Kibana | Kibana Guide | Elastic
- Set telemetry.enabled to false
- Is there a way to disable news feed · Issue #51630 · elastic/kibana
- Set newsfeed.enabled to false