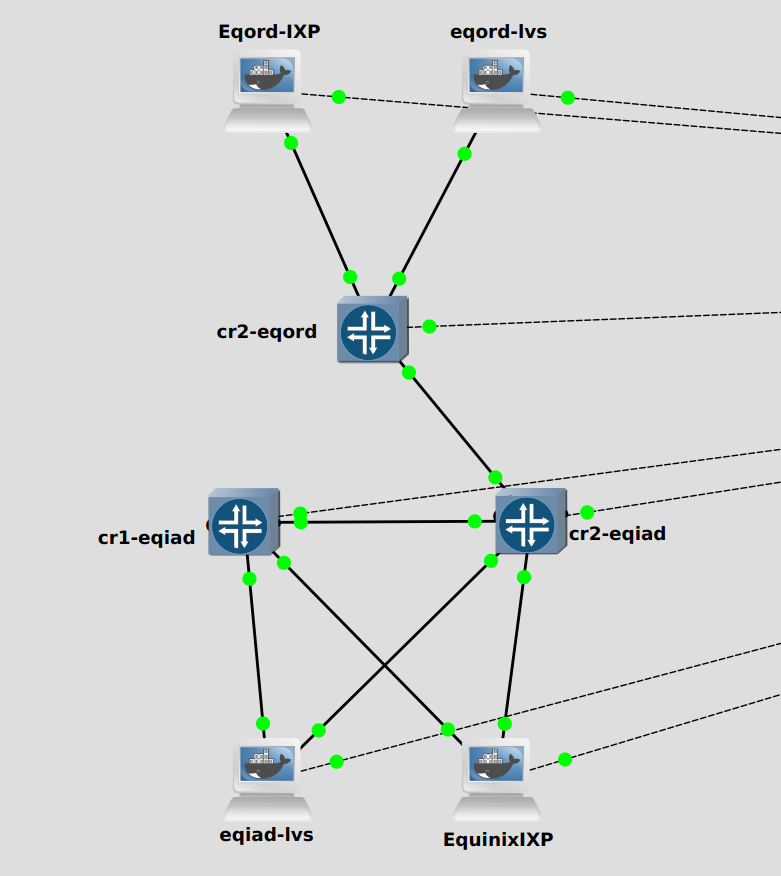
As pointed out by @cmooney, using next-hop-self on advertisements between iBGP peers (core routers) should solve the Equinix Ashburn IXP issue (see T295650 and T293726#7454820).
Even if IX_PEER_A is directly reachable from cr1 and cr2, if it only peers with cr2, the prefixes will be sent from cr2 to cr1 with cr2's IP as next-hop (instead of IX_PEER_A's IP previously).
Another way to put it is that traffic will follow the BGP sessions.
Turning up peering with IX_PEER_A on cr1 will make that peer redundant as now cr1 will send traffic directly to that peer.
I can't think of any downside, but this needs to be carefully rolled out. Maybe de-pooling ulsfo then testing the change there.
https://wikitech.wikimedia.org/wiki/Incidents/2021-10-22_eqiad_return_path_timeouts
https://wikitech.wikimedia.org/wiki/Incidents/2021-11-23_Core_Network_Routing