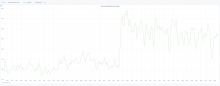
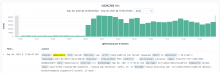
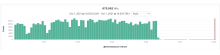
I've noticed that since around 16:02-16:06 yesterday, there is a large amount (50% increase in logged messages, compared to the baseline) of extra error logs.
They appear to be coming from failed CirrusSearch jobs: "ElasticaWrite job failed" and "Failed executing job: cirrusSearchElasticaWrite".
At first I reported it at T48643#7394374 but as it didn't match the wikis affected, I was told it was unrelated to Wikidata. The fact that it is mostly only CirrusSearch jobs confirms that.
This is the jobqueue channel at that time:
https://logstash.wikimedia.org/goto/263ff9c2e9bdb0668b0864f9cebdb0d5