T197279 - Directly POSTing to Special:ChangeEmail would allow for bypassing reauthentication, allowing for potential account takeover.
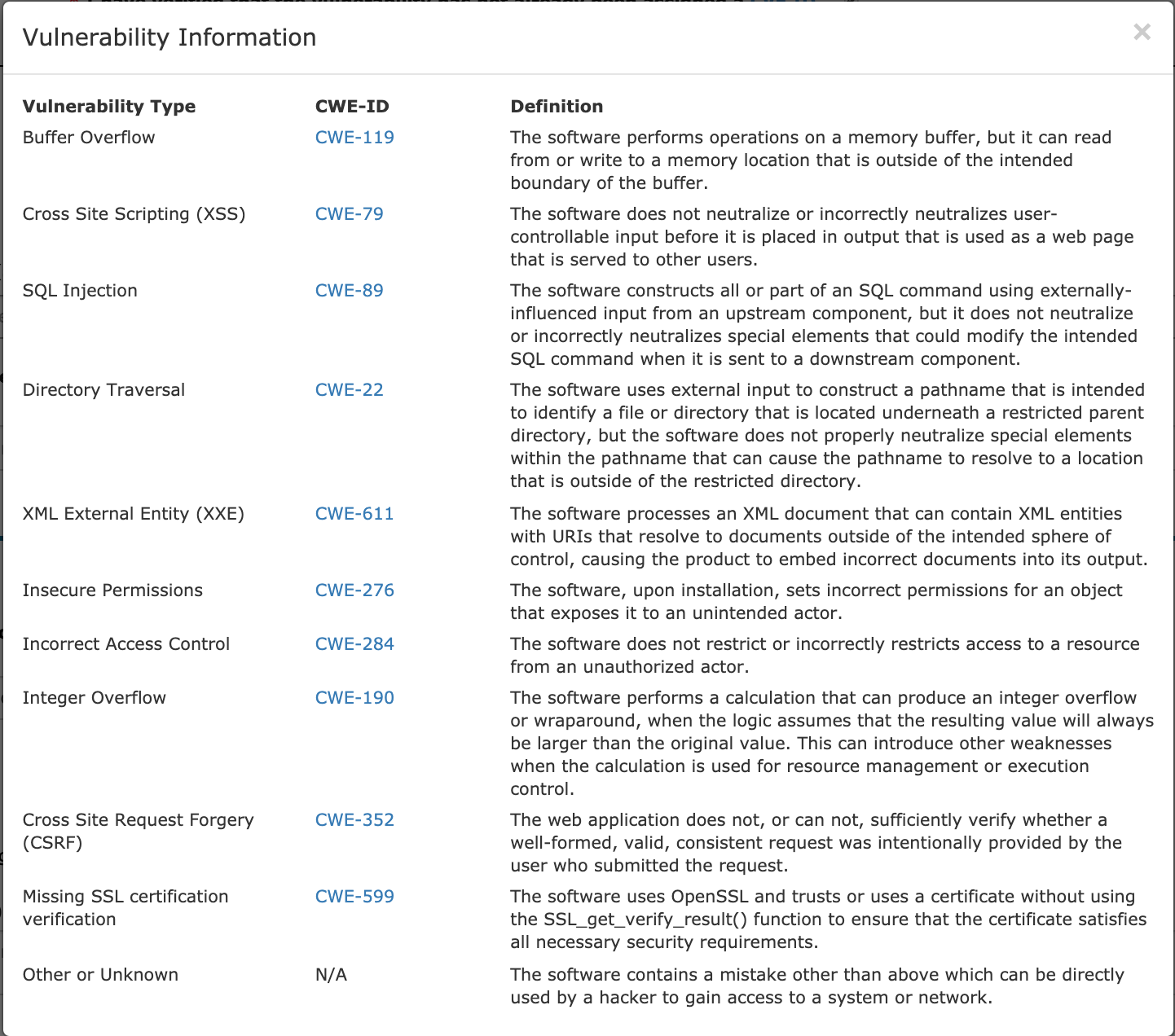
Vulnerability type: Incorrect Access Controls
Affects all MediaWiki versions since 1.27.0 (Jun 2016)
CVE-2019-12468
T204729 - Passing invalid titles to the API could cause a DoS by querying the entire watchlist table.
Vulnerability type: Other
Affects all MediaWiki versions since 1.27.0 (Jun 2016)
CVE-2019-12473
T207603 - Loading user JavaScript from a non-existent account allows anyone to create the account, and XSS the users' loading that script.
Vulnerability type: XSS
Affects all MediaWiki versions since 1.3.0 (August 2004) if $wgAllowUserJs is enabled (it defaults to false since 1.3.10).
CVE-2019-12471
T199540 - It is possible to bypass the limits on IP range blocks ($wgBlockCIDRLimit) by using the API.
Vulnerability type: Incorrect Access Controls
Affects all MediaWiki versions since 1.18.0 (November 2011).
CVE-2019-12472
T212118 - Privileged API responses that include whether a recent change has been patrolled may be cached publicly
Vulnerability type: Other
Affects all MediaWiki versions since 1.23.0 (June 2014).
CVE-2019-12474
T209794 - A spammer can use Special:ChangeEmail to send out spam with no rate limiting or ability to block them.
Vulnerability type: Incorrect Access Controls
Affects all MediaWiki versions. (I think...)
CVE-2019-12467
T25227 - An account can be logged out without using a token (CSRF)
Vulnerability type:
Affects all MediaWiki versions.
CVE-2019-12466
T222036 - Exposed suppressed username or log in Special:EditTags
Vulnerability type: Incorrect Access Controls
CVE-2019-12469
T222038 - Exposed suppressed log in RevisionDelete page
Vulnerability type: Incorrect Access Controls
Affects
CVE-2019-12470
Not requesting a CVE for T208881 which seems like an issue in browsers, not MediaWiki.
Not requesting a CVE for T207916, which is about improving our auditing and logging.