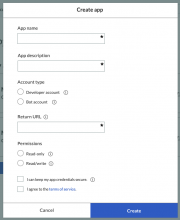
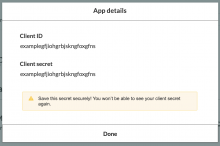
The create app flow allow users to register a client with the API Portal.
Status: Getting feedback on proposed form
Prototype
Prerequisites
- User must be logged in to the API Portal with a Wikimedia account
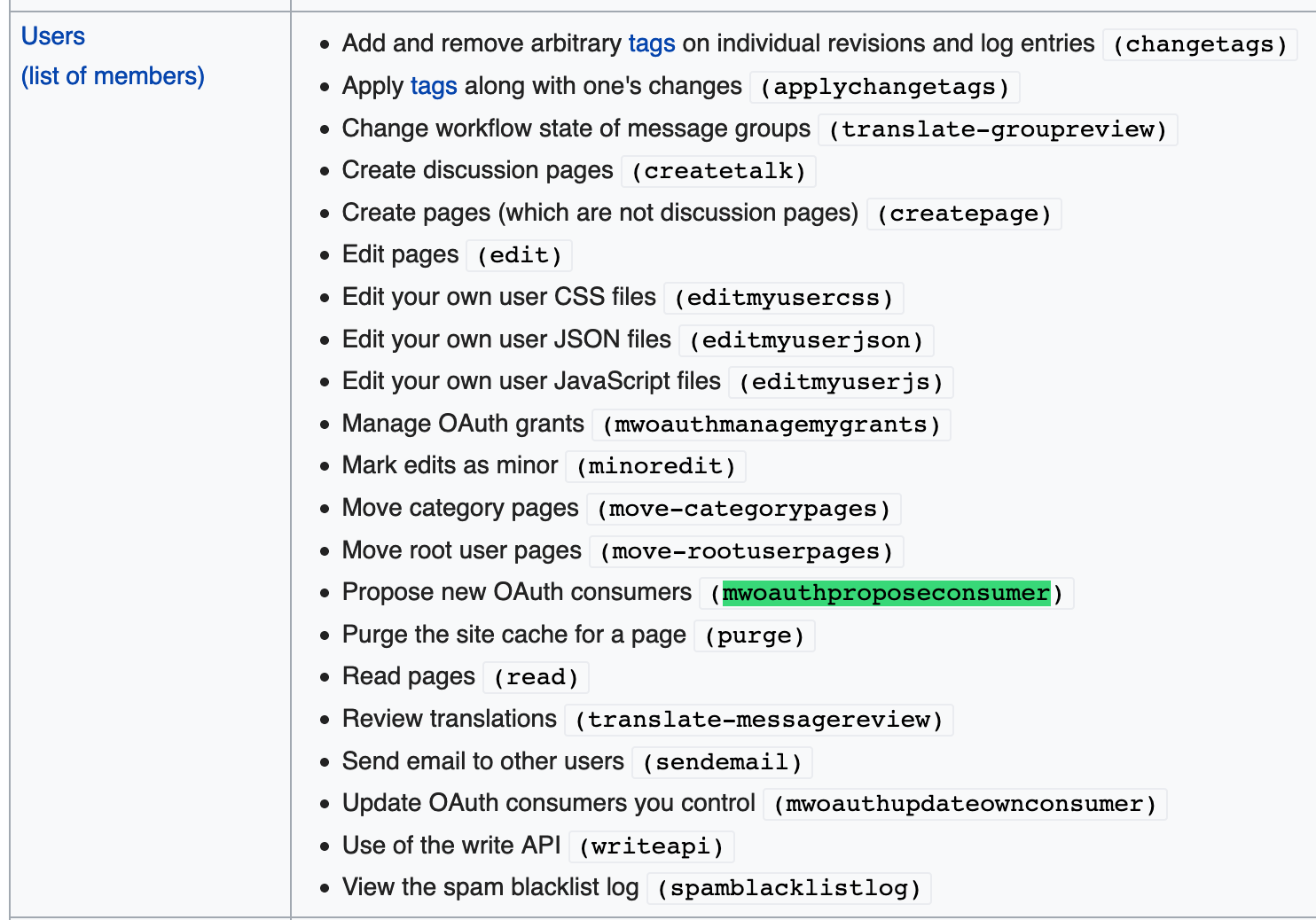
- User must have the mwoauthproposeconsumer right (Automatically granted to all users)
- User must have a confirmed email address
Form fields
All fields are required.
- App name
- App description
- Account type
- Selecting "Developer account" unchecks the owner-only client option and submits "authorization_code", "refresh_token", and "client_credentials" as the grant types
- Selecting "Bot account" checks the owner-only client option and removed the "Return URL" field
- Return URL (only required for developer accounts)
- Permissions
- Read: applies basic, highvolume, viewdeleted, and oversight grants
- Read/Write: applies basic, highvolume, viewdeleted, oversight, and createeditmovepage grants
- "Client is confidential" checkbox
- User agreement checkbox
Map between rights used by the MediaWiki REST API and grant types
| Right | Grant Type(s) | Handler(s) |
|---|---|---|
| read | basic | various |
| writeapi | basic | various |
| bot | highvolume | PageHistoryCountHandler |
| deletedhistory | viewdeleted | PageHistoryHandler |
| suppressrevision | oversight | PageHistoryHandler |
| edit | editpage, createeditmovepage, and others | CreationHandler/UpdateHandler |
Map between fields on Meta and fields in the API Portal
| Field | Required | Val | DB | Default | API Portal |
|---|---|---|---|---|---|
| Name | Yes | name | oarc_name | none | User-entered, required |
| Description | Yes | description | oarc_description | none | User-entered, required |
| Owner-only client checkbox | “This consumer is for use only by [Username]” | User-entered, required | |||
| Callback URL | Yes | callbackUrl | oarc_callback_url | none | User-entered, not required for owner-only clients |
| Confidential checkbox | No | oauth2IsConfidential | oarc_oauth2_is_confidential | Yes | User-entered, required |
| OAuth2 Grant Types | No | oauth2GrantTypes | oarc_oauth2_allowed_grants | [“authorization_code”,”refresh_token”] | User-entered, either:auth code flow ( "authorization_code", "refresh_token") or client credentials flow: ("client_credentials") |
| Grants | Yes | grants | oarc_grants | (some basic permissions) | User-entered. Read: basic, highvolume, viewdeleted, oversight. Read/Write: basic, highvolume, viewdeleted, oversight, createeditmovepage |
| Agreement | Yes | developerAgreement | oarc_developer_agreement | None (user must agree) | User-entered, include as-is |
| Yes | oarc_email | Wiki email | Omit and revert to default | ||
| Wiki | Yes | wiki | oarc_wiki | * | Omit and revert to default |
| Grant Type“Types of grants being requested:” | Yes | granttype | N/A | normal | Omit and default to “Request authorization for specific permissions.” |
| Version | Yes | version | oarc_version | 1.0 | Omit and revert to default |
| Allowed IP ranges | Omit and revert to default | ||||
| OAuth version | Omit, always 2.0 | ||||
| Callback prefix checkbox | Yes | “Allow consumer to specify a callback in requests and use "callback" URL above as a required prefix.” | Omit and revert to checked. Doesn’t apply to OAuth 2.0. | ||