Hello Release-Engineering-Team -
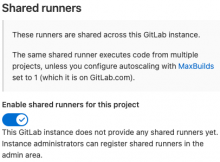
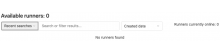
It looks like runners have been completely disabled for gitlab.wikimedia.org at this time?
I assume this might be related to the ongoing discussion at T291978 etc? Is there a plan to enable any variety of runners soon? If not, I'd like to request that perhaps 2 to 3 runners be enabled for pipelines under the security group within Gitlab so that we have an easy means to continue testing and developing our security ci templates this quarter and next. Thanks.