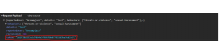
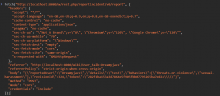
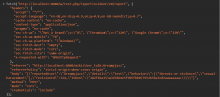
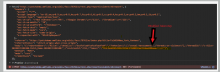
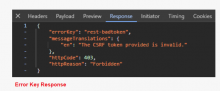
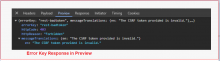
The Incident-Reporting-System extension provides a REST API used to make incident reports. These reports are made via a POST request and cause an email to be sent with the contents of the report after validation and rate limiting.
However, this REST API does not validate a CSRF token and nor does it require that the user making the request use a session that is safe from CSRF (such as OAuth).