It seems someone is scanning wikis for SQL injection or other vulnerability related to improper string escaping. It is worth confirming that the code is not vulnerable.
The requests look like this:
/wiki/Special:Log?page=20&tagfilter=17&type=import&user=91.247.38.47&wpdate=%bf'%bf%22&wpfilters%5b%5d=review
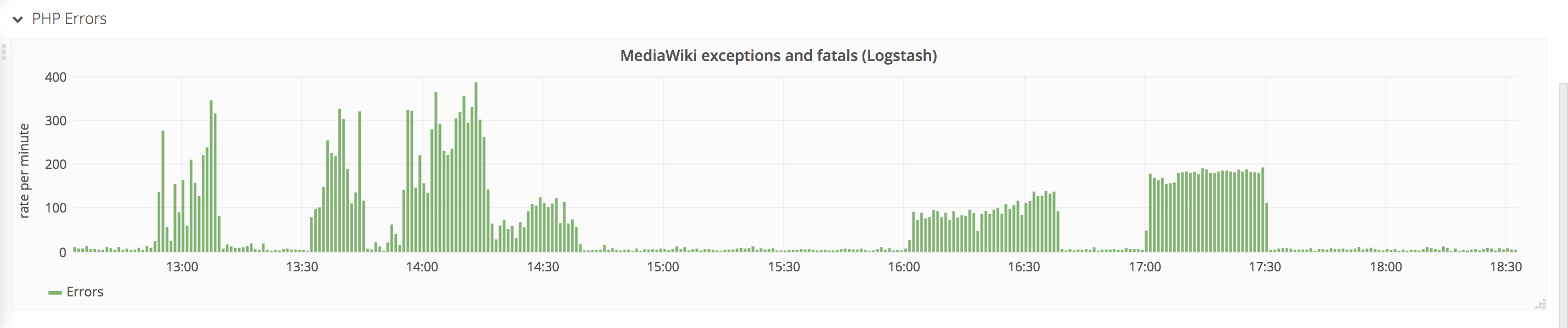
https://logstash.wikimedia.org/goto/9f09650b6089006d15a8b47c4cebc245 (note this only captures the ones of this format, and not successful ones)
And we get errors such as:
Invalid timestamp - ¿'¿" 00:00:00 Invalid timestamp - @@GpY50 00:00:00 Invalid timestamp - JyI= 00:00:00 Invalid timestamp - (select convert(int,CHAR(65))) 00:00:00
Please have a look if this is blind testing with no impact and should be ignored, or if it is a known or 0 day exploitation (but clumsy execution).
Update: Probably the same person started later to do the same on enwiki, with a different function:
/w/index.php?associated=1&invert=1&namespace=-1;select%20pg_sleep(7);%20--%20&tagfilter=17&target=Main%20Page&title=Special:RecentChangesLinked MWException from line 64 of /srv/mediawiki/php-1.32.0-wmf.15/includes/MWNamespace.php: MWNamespace::getAssociated does not make any sense for given namespace -1
And wikiquote before:
https://en.wikiquote.org/wiki/Special:Log?page=20&subtype=create&tagfilter=17&type=abusefilter&user=91.247.38.47&wpdate=-0001-11-30