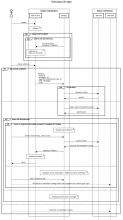
Problem:
Sometimes we can't let certain edits happen. This might be because:
- article is protected
- Item is protected
- user/ip is blocked on client
- user/ip is blocked on repo
Ideally we don't want to let them make the edit and then have it be rejected by the API afterwards. Instead we want to intervene as early as possible by for example not showing them the edit link, or less ideally showing a message in the Bridge modal.
We need to figure out what is technically possible. New Lua function? API check?
Acceptance criteria:
- we have a recommendation for how to handle the 4 cases above and the documentation of the investigated ideas
Open questions:
- user specific vs. caching?!
Timeboxing this for 2 days - ideally 2 people (1 person per day)