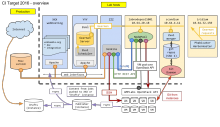
gallium has lost its disk and an attempt is made to recover it. Meanwhile we had a new server installed contint1001.wikimedia.org with IP 208.80.154.17 . We would need firewall rules to be added to let servers in the labs support network to be able to reach the new server. The existing rules to gallium 208.80.154.135 should be kept.
Gives an overview, with the three blue box which could be considered as services running on contint1001.wikimedia.org
Flows were previously documented on https://www.mediawiki.org/wiki/Continuous_integration/Architecture/Isolation#Security_matrix when we had labnodepool1001.eqiad.wmnet set up.
Flows going to contint1001
| Works? | Proto | source host | source IP | dest Host | dest IP | dest port | description |
|---|---|---|---|---|---|---|---|
| TCP | scandium | 10.64.4.12 | contint1001 | 208.80.154.17 | 4730 | zuul merger to zuul gearman server | |
| TCP | labnodepool1001 | 10.64.20.18 | contint1001 | 208.80.154.17 | 4730 | Nodepool to zuul gearman server | |
| xxx | TCP | iridium | 10.64.32.150 | contint1001 | 208.80.154.17 | 4730 | Phabricator to zuul gearman server. Removed via https://gerrit.wikimedia.org/r/#/c/310039/ |
| TCP | labnodepool1001 | 10.64.20.18 | contint1001 | 208.80.154.17 | 8888 | Nodepool to Jenkins ZeroMQ | |
| TCP | labnodepool1001 | 10.64.20.18 | contint1001 | 208.80.154.17 | 443 | Nodepool to Jenkins REST API | |
Flows originating from contint1001
| Works ? | Proto | source host | source IP | dest Host | dest IP | dest port | description |
|---|---|---|---|---|---|---|---|
| TCP | contint1001 | 208.80.154.17 | scandium | 10.64.4.12 | 9418 | Git connection to Zuul-merger git daemon | |
| TCP | contint1001 | 208.80.154.17 | contintcloud instances | 10.x.x.x/y | 22 | Jenkins server/client connection to slaves | |
| TCP | contint1001 | 208.80.154.17 | contintcloud instances | 10.x.x.x/y | 873 | rsync | |
| ??? | UDP | contint1001 | 208.80.154.17 | statsd.eqiad.wmnet | ??? | 8125 | Zuul scheduler metrics to statsd |