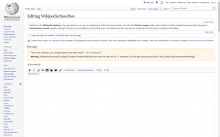
Steps to reproduce:
- Enable live preview ("Show previews without reloading the page")
- Open the edit form (e.g. Wikipedia:Sandbox)
- Pass multiple arguments to the same parameter in a template (e.g. {{tl|1=|1=}}) and hit Show preview
Actual results:
- The warning box says "Warning: [[:Wikipedia:Sandbox]] is calling [[:Template:Template link]] with more than one value for the "1" parameter. Only the last value provided will be used. ([[Help:Duplicate parameters|Help]])"
Expected results:
- It says "Warning: Wikipedia:Sandbox is calling Template:Template link with more than one value for the "1" parameter. Only the last value provided will be used. (Help)", as it does with the live preview turned off
I believe line 273 of mediawiki.action.edit.preview.js should be
$previewHeader.find( '.warningbox' ).append( $( '<p>' ).msg( warning ) );
instead of
$previewHeader.find( '.warningbox' ).append( $( '<p>' ).append( warning ) );
though there may be a sleeker solution.
It seems this was introduced in either T190120 or T266311, so pinging their assignees.