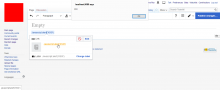
Steps to reproduce:
- Open VisualEditor
- Create an internal link with "Javascript:alert('XSS!')" as the target
- Place cursor inside the link
- Click on the link preview in the context menu
Note that this issue does not occur when the link already exists on the page when you open it for editing. Such link correctly links to a page titled "Javascript:alert('XSS!')". It only occurs for links you place yourself while editing. As far as I can tell, there is no "real" XSS here, but possibly it could be abused by a creative attacker.
Note also that this is an obvious extension of this publicly reported issue: T206231: Link in link popup has incomplete target URL if page contains namespace.