Summary
The Security-Team recently completed an audit of the configuration file maintain-views.yaml, in order to explore whether wiki-replicas pose some privacy risks for the contributors supporting Wikimedia projects. As part of the conclusions, it is recommended that latitude and longitude of Commons images be redacted from replicas.
Broader context
Some of the image files uploaded to commons include longitude and latitude coordinates in the metadata, as per the result of the query below. This practice is well established among the Wikimedia commons community and has various applications. However, this may pose privacy risks for authors of images that are geolocated, as malign actors may deduce their likely location, if they happen to take a certain number of images from a specific area. While this may seem an edge case, the risks associated with that eventuality warrant some measures. Below is a SQL query disclosing the latitude and longitude of places volunteers have been, based on the geolocation information associated with an image they uploaded to Commons.
SELECT img_name, img_metadata, actor_name FROM image LEFT JOIN actor ON img_actor = actor_id LIMIT 100;
Acceptance Criteria
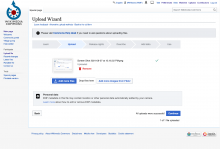
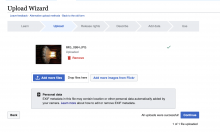
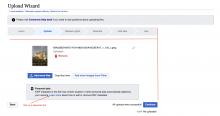
- On the "Upload" page of the Upload Wizard, a message appears that says "Personal data: EXIF metadata in this file may contain location or other personal data automatically added by your camera. Learn more about how to edit or remove EXIF metadata."
- The message appeared once an image has been added, but before published
- The message shows on all uploads, regardless of if EXIF data exists
- The message appears as depicted in this mockup