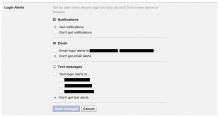
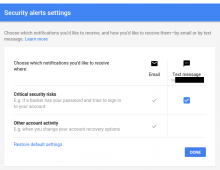
Create an opt-in email notification when a user logs in for a new device. This is for admins and active editors who are worried about getting hacked.
The notification is off by default, opt-in under the Notifications tab.
Definition of "new device" is the same as LoginNotify. There's a cookie per device, which lasts for 90 days since the last time you logged in with that device.
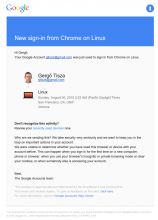
Email:
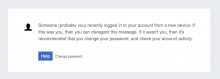
Someone (probably you) recently logged in to your account from a new device. If this was you, then you can disregard this message. If it wasn't you, then it's recommended that you change your password, and check your account activity.
Help information: https://mediawiki.org/wiki/Help:Login_notifications?markasread=60
Change password: http://core.local/index.php/Special:ChangePassword
original ticket:
Most large sites (Facebook, Google etc.) offer some kind of alert when someone logs in to an account from a new machine - it's a good way of protecting against account theft:
I wonder if something like that would make sense for MediaWiki? Ie.
- put the one.way hashed username in a cookie with very long expiration
- after a successful login check for the presence of the cookie
- if it's there, update the expiration date
- if it's not there, and the user requested alerts, send an email with the IP and other details of the login.