Background
In T263756: Create a table to store which users have access to IPInfo, and the timestamp when access was granted [L], Anti-Harassment decided to log the desired log lines to Special:Log. T292842: Log when the user's access level changes, T294657: Create a log entry when the LogHandler is called, and T294658: Create a log entry when the RevisionHandler is called cover logging those log lines. This task covers displaying those log lines on Special:Log.
AC
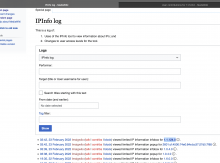
- The ipinfo log can be viewed on Special:Log
- The ipinfo log is only visible to users with the ipinfo-view-log right (will be assigned to WMF staff and CheckUser users in a separate task)
- Log lines in the ipinfo log are formatted as follows:
| Action | Example |
|---|---|
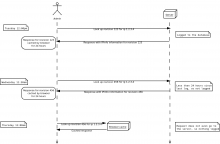
| User A viewed information about 1.1.1.1 with basic access via the popup | User:A viewed limited IP Information popup for 1.1.1.1 at $time |
| User B viewed information about 2.2.2.2 with full access via the popup | User:B viewed full IP Information popup for 2.2.2.2 at $time |
| User C viewed information about 3.3.3.3 with basic access via the infobox | User:C viewed limited IP Information infobox for 3.3.3.3 at $time |
| User D viewed information about 4.4.4.4 with full access via the infobox | User:D viewed full IP Information infobox for 4.4.4.4 at $time |
- No log entry appears if the user had the ipinfo right but no rights to see any information
Notes
- https://gerrit.wikimedia.org/r/c/mediawiki/extensions/IPInfo/+/736267 demonstrates how to add the IPInfo log to Special:Log and associate the \MediaWiki\Extensions\IPInfo\Logging\LogFormatter log formatter with all ipinfo log lines
- You can read about displaying log lines on Special:Log here: https://www.mediawiki.org/wiki/Special:MyLanguage/Manual:Logging_to_Special:Log
- You can find examples of log formatters here: https://www.mediawiki.org/wiki/Manual:$wgLogActionsHandlers
- You can read about restricting access to specific log lines here: https://www.mediawiki.org/wiki/Manual:$wgLogRestrictions