Problem
Blocks can be evaded by changing the IP address (intentionally or unwittingly) so IP range blocks are often used to stop block evasions. However, these can cause collateral damage by preventing good-faith innocent bystanders from editing. If an additional piece of data was used in addition to IP range, it could result in more (or wider) IP range blocks being set with less collateral damage.
CheckUsers can currently see User Agent information in their work. While this can also be spoofed, it is a reliable piece of information we're already collecting.
Proposed solution
Allow IP addresses, particularly IP ranges, to be blocked via user-agent in addition to the IP address/range. CheckUsers should be the only group to use this function.
Acceptance criteria
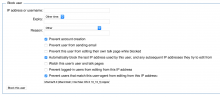
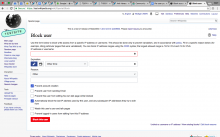
- On Special:Block, introduce a new checkbox to allow blocking by User Agent in addition to IP
- This option should only appear to CheckUsers (has the checkuser right, or may want to introduce a new right)
- This option should only appear if an IP address or IP range is provided in the 'user' field
- The default should be unchecked (off) with a disabled text input box next to it.
- The text input box should become active if the checkbox is checked
- Label for preference Only block devices that match this user agent
- Add a OOUI help tip to describe this feature. Text TBD.
- If a user is editing within the IP address or IP range of this type of block...
- ...if their user agent matches, they should be blocked from editing, as current blocks work.
- ...if their user agent does not match, they should be allowed to edit with no warnings or notices.
- Visiting Special:Block on a currently blocked user:
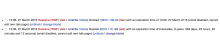
- If a CheckUser goes to Special:Block to update the block, they should see the UA in the text area and update it and re-save the block.
- If an admin (or someone else with block permissions without UA block permissions) goes to Special:Block to update the block:
- they should see there is a UA block but not be able to see the contents of or edit the UA text area.
- they should be able to adjust the rest of the block parameters
- Log entry
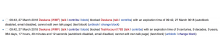
- In the log entry (on Special:Log, Special:Block, etc.) the block should be marked as CU filtered
- e.g. 12:34, 23 March 2018 Foobar (talk | contribs | block) blocked 000.0.0.000 (talk | contribs) with an expiration time of N (anon. only, account creation blocked, CU filtered) (block reason) (unblock | change block)
- If the block is updated, the log should reflect if the UA portion of the block was changed.
Mockup
Potential future improvements
- Data validation on save to ensure an ineffective block is being set
- Support regex
- URL parameter(s) to automatically check the box and fill in the text field