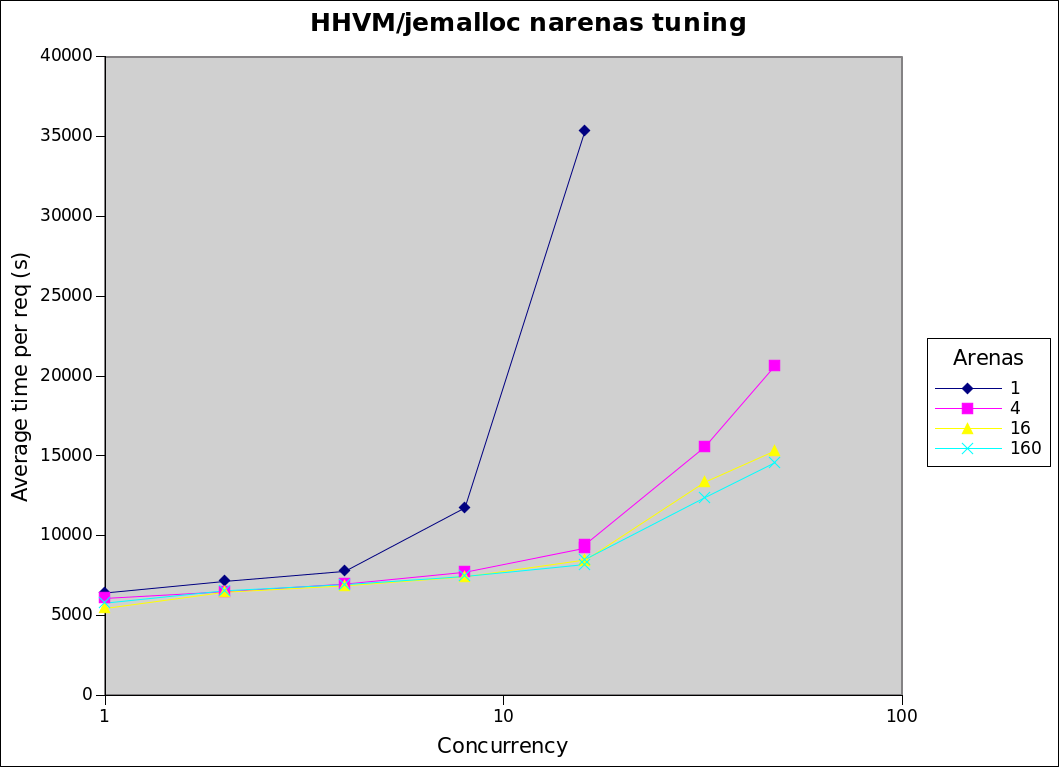
At around 2.00 UTC on 27/11/2016 the api appservers started using more and more memory and eventually throw enough errors and page at 2.27 UTC 02:27 -icinga-wm:#wikimedia-operations- PROBLEM - LVS HTTP IPv4 on api.svc.eqiad.wmnet is CRITICAL: CRITICAL - Socket timeout after 10 seconds
I've captured some hhvm backtraces on e.g. mw1279 in /root and roll-restarted api_appcluster which *seems* to have helped a bit.
Taking a closer look there seemed to be failing requests for euwiki from parsoid (from apache access log), among other failing requests. The requests for euwiki seemed to be continuing failing even after the rolling restart.
2016-11-27T02:02:53 119996827 10.64.32.74 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.32.74
2016-11-27T02:02:55 119997898 10.64.32.89 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.32.89
2016-11-27T02:03:04 119992080 10.64.0.215 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.0.215
2016-11-27T02:03:09 119996351 10.64.0.215 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.0.215
2016-11-27T02:03:09 119991462 10.64.32.84 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.32.84
2016-11-27T02:03:16 119994184 10.64.32.90 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.32.90
2016-11-27T02:03:18 119990649 10.64.0.218 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.0.218
2016-11-27T02:03:19 119986385 10.64.0.215 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.0.215
2016-11-27T02:03:20 119999445 10.64.32.78 proxy-server/503 50065 GET http://eu.wikipedia.org/w/api.php
- text/html - - Parsoid/0.6.1 - - - 10.64.32.78In logstash there were logs related to dbquery for euwiki, e.g. (shortlink https://logstash.wikimedia.org/goto/4b7ce91a52c4feef185a3075d31162d9)
Database::query: lost connection to 10.64.32.136; reconnected:
#0 /srv/mediawiki/php-1.29.0-wmf.3/includes/libs/rdbms/database/Database.php(1254): Database->query()
#1 /srv/mediawiki/php-1.29.0-wmf.3/includes/libs/rdbms/database/Database.php(1322): Database->select()
#2 /srv/mediawiki/php-1.29.0-wmf.3/includes/cache/LinkCache.php(296): Database->selectRow()
#3 /srv/mediawiki/php-1.29.0-wmf.3/includes/cache/LinkCache.php(267): LinkCache->fetchPageRow()
#4 /srv/mediawiki/php-1.29.0-wmf.3/includes/Title.php(3209): LinkCache->addLinkObj()
#5 /srv/mediawiki/php-1.29.0-wmf.3/includes/Title.php(934): Title->getArticleID()
#6 /srv/mediawiki/php-1.29.0-wmf.3/includes/Title.php(955): Title->getContentModel()
#7 /srv/mediawiki/php-1.29.0-wmf.3/extensions/Scribunto/common/Hooks.php(94): Title->hasContentModel()
#8 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3379): ScribuntoHooks::invokeHook()
#9 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3103): Parser->callParserFunction()
#10 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#11 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3021): PPFrame_Hash->expand()
#12 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#13 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1448): PPFrame_Hash->expand()
#14 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3253): PPTemplateFrame_Hash->cachedExpand()
#15 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#16 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3021): PPFrame_Hash->expand()
#17 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#18 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3256): PPFrame_Hash->expand()
#19 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#20 /srv/mediawiki/php-1.29.0-wmf.3/extensions/ParserFunctions/ParserFunctions_body.php(104): PPFrame_Hash->expand()
#21 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3379): ExtParserFunctions::ifObj()
#22 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3103): Parser->callParserFunction()
#23 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#24 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1528): PPFrame_Hash->expand()
#25 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1540): PPTemplateFrame_Hash->getNamedArgument()
#26 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3759): PPTemplateFrame_Hash->getArgument()
#27 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1032): Parser->argSubstitution()
#28 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1528): PPFrame_Hash->expand()
#29 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1540): PPTemplateFrame_Hash->getNamedArgument()
#30 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3759): PPTemplateFrame_Hash->getArgument()
#31 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1032): Parser->argSubstitution()
#32 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3021): PPFrame_Hash->expand()
#33 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#34 /srv/mediawiki/php-1.29.0-wmf.3/extensions/ParserFunctions/ParserFunctions_body.php(106): PPFrame_Hash->expand()
#35 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3379): ExtParserFunctions::ifObj()
#36 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3103): Parser->callParserFunction()
#37 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#38 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3256): PPFrame_Hash->expand()
#39 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#40 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3256): PPFrame_Hash->expand()
#41 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#42 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(3256): PPFrame_Hash->expand()
#43 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Preprocessor_Hash.php(1015): Parser->braceSubstitution()
#44 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(2917): PPFrame_Hash->expand()
#45 /srv/mediawiki/php-1.29.0-wmf.3/includes/parser/Parser.php(654): Parser->replaceVariables()
#46 /srv/mediawiki/php-1.29.0-wmf.3/includes/StubObject.php(113): Parser->preprocess()
#47 /srv/mediawiki/php-1.29.0-wmf.3/includes/StubObject.php(139): StubObject->_call()
#48 /srv/mediawiki/php-1.29.0-wmf.3/extensions/ParsoidBatchAPI/includes/ApiParsoidBatch.php(174): StubObject->__call()
#49 /srv/mediawiki/php-1.29.0-wmf.3/extensions/ParsoidBatchAPI/includes/ApiParsoidBatch.php(82): ApiParsoidBatch->preprocess()
#50 /srv/mediawiki/php-1.29.0-wmf.3/includes/api/ApiMain.php(1434): ApiParsoidBatch->execute()
#51 /srv/mediawiki/php-1.29.0-wmf.3/includes/api/ApiMain.php(510): ApiMain->executeAction()
#52 /srv/mediawiki/php-1.29.0-wmf.3/includes/api/ApiMain.php(481): ApiMain->executeActionWithErrorHandling()
#53 /srv/mediawiki/php-1.29.0-wmf.3/api.php(83): ApiMain->execute()
#54 /srv/mediawiki/w/api.php(3): include()
#55 {main}