Update
We have reached consensus that all authorised users in Superset should be allocated the sql_lab role or equivalent, in addition to the standard Alpha role.
This task is now primarily about implementing that set of default permissions.
In the meantime, any users who still lack that role may request it below and any Superset admin may add it.
Summary
This is a follow-up ticket from T328152: Some users' presto queries are no longer working in Superset in which we discovered that the certain bugs in the permission system had been fixed in version 1.5.3.
The impact of this fix in version 1.5 is that the permissions are now applied correctly, preventing users from running queries that thay had been able to run under previous versions.
By default, when users are created in Superset, they are granted the Alpha role.
Alpha users have access to all data sources, but they cannot grant or revoke access from other users. They are also limited to altering the objects that they own. Alpha users can add and alter data sources.
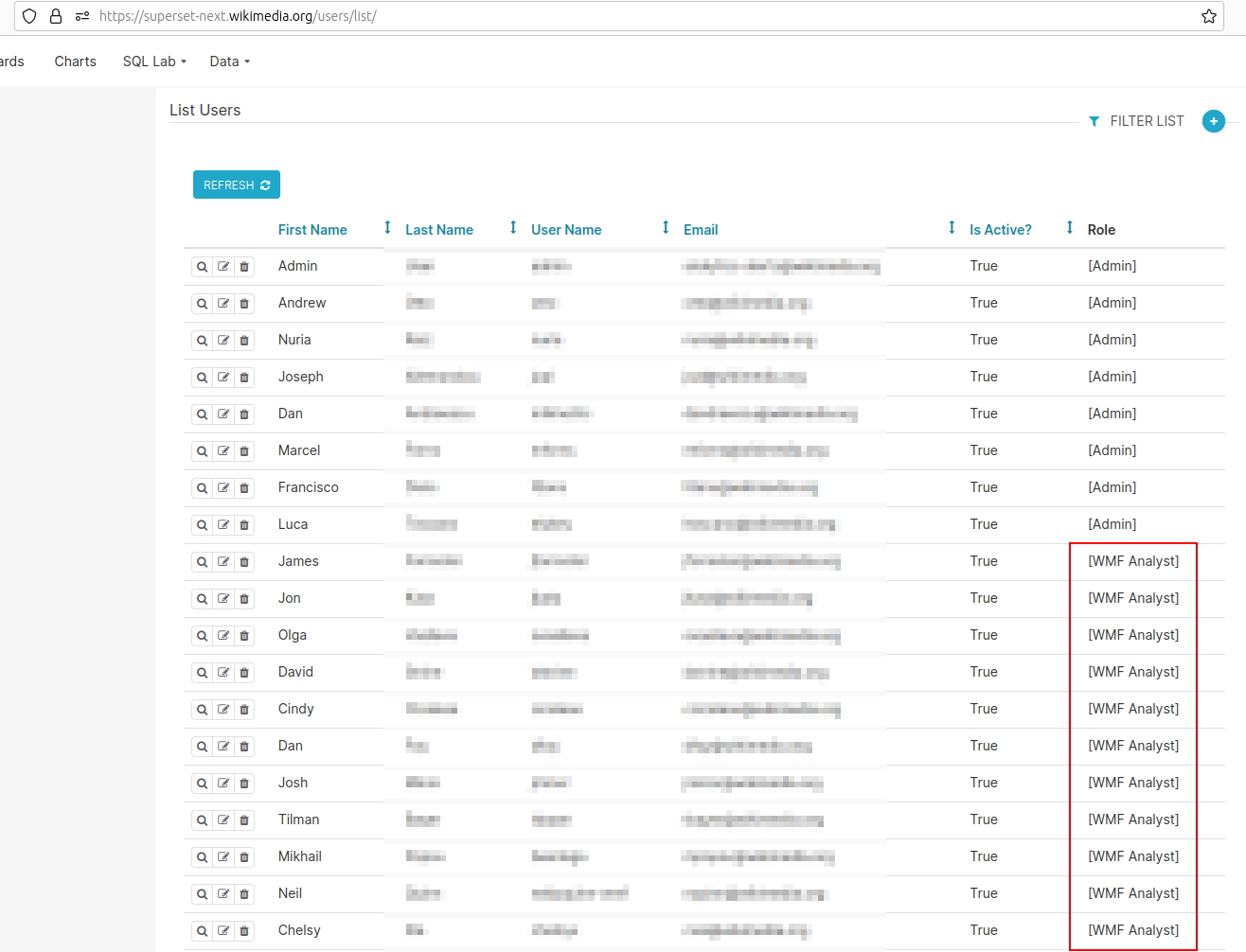
However, they are not by default granted the sql_lab role.
The sql_lab role grants access to SQL Lab. Note that while Admin users have access to all databases by default, both Alpha and Gamma users need to be given access on a per database basis.
What happened in T328152 is that users were still able to access SQL Lab by using saved links or bookmarks, but they were prevented from running queries. Errors appeared with very limited information, saying Database Error, unknown error.
Since all of the users who raised the issue had legitmate causes to access SQL Lab, we granted the sql_lab role immediately, which resolved the issue.
However, we should review how we assign these privileges and define a policy.
Tasks
- Decide who should be granted access to SQL Lab in Superset
- Decide who should be granted Admin rights in Superset
- Decide whether or not any other roles are required, other than the default roles
- Document the procedures of requesting/revoking access to various Superset roles
- Ensure that the permissions in production match those defined in the policies
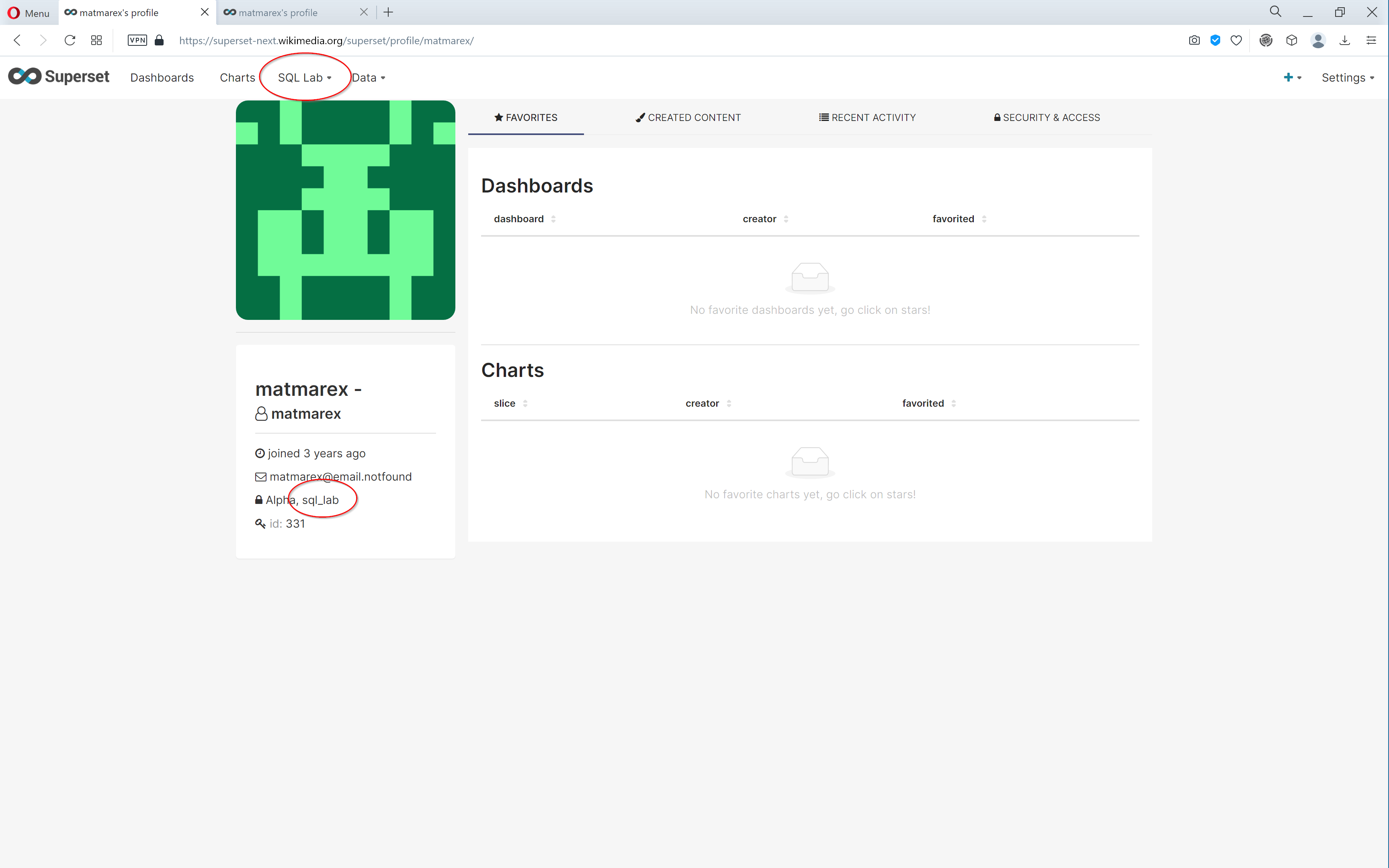
A user with the Alpha and sql_lab roles applied
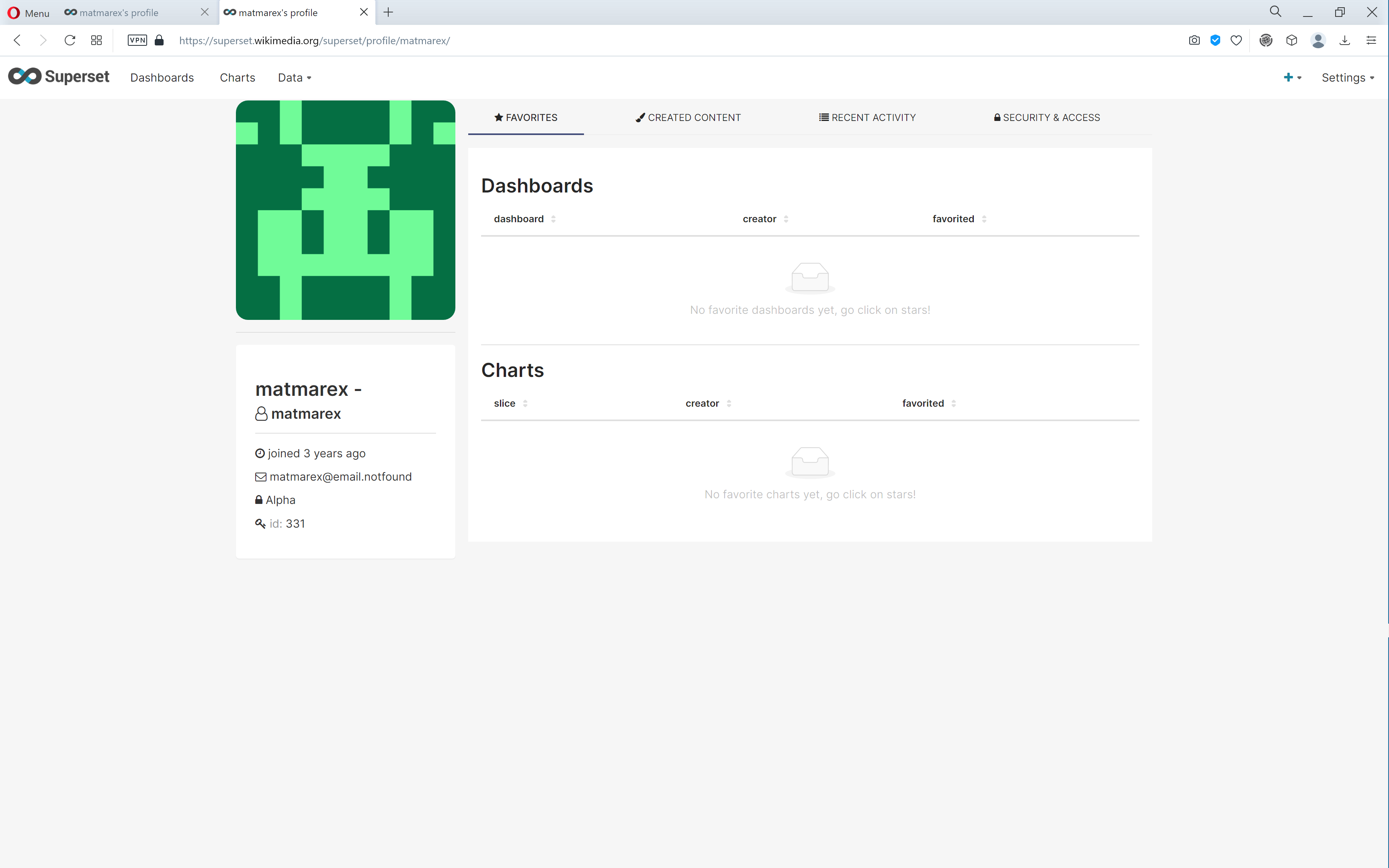
A user with only the Alpha role applied