What's the problem?
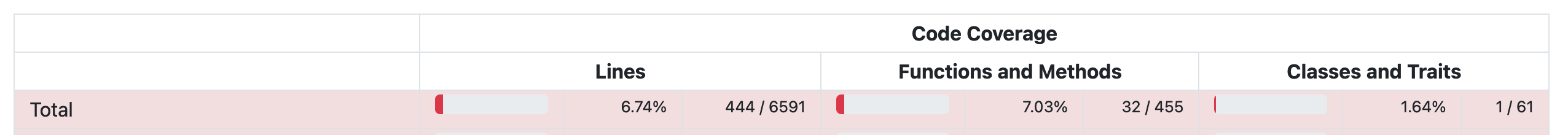
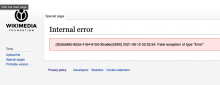
SecurePoll is running into a "DBTransactionSizeError" when trying to create an election.
In T287780#7251685, @dom_walden wrote:@Reedy @Zabe @Majavah Trying to create an election with "All wiki" selected on votewiki and testwiki, get some sort of timeout:
[19e3148a-a7d9-4c40-9aa2-bf5e49d774e1] /wiki/Special:SecurePoll/create Wikimedia\Rdbms\DBTransactionSizeError: Transaction spent 4.2640490531921 second(s) in writes, exceeding the limit of 3 Backtrace: from /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/loadbalancer/LoadBalancer.php(1748) #0 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/loadbalancer/LoadBalancer.php(2265): Wikimedia\Rdbms\LoadBalancer::Wikimedia\Rdbms\{closure}(Wikimedia\Rdbms\DatabaseMysqli) #1 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/loadbalancer/LoadBalancer.php(1762): Wikimedia\Rdbms\LoadBalancer->forEachOpenMasterConnection(Closure) #2 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/lbfactory/LBFactory.php(249): Wikimedia\Rdbms\LoadBalancer->approveMasterChanges(array, string, integer) #3 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/lbfactory/LBFactoryMulti.php(236): Wikimedia\Rdbms\LBFactory::Wikimedia\Rdbms\{closure}(Wikimedia\Rdbms\LoadBalancer, string, array) #4 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/lbfactory/LBFactory.php(251): Wikimedia\Rdbms\LBFactoryMulti->forEachLB(Closure, array) #5 /srv/mediawiki/php-1.37.0-wmf.16/includes/libs/rdbms/lbfactory/LBFactory.php(310): Wikimedia\Rdbms\LBFactory->forEachLBCallMethod(string, array) #6 /srv/mediawiki/php-1.37.0-wmf.16/includes/MediaWiki.php(684): Wikimedia\Rdbms\LBFactory->commitMasterChanges(string, array) #7 /srv/mediawiki/php-1.37.0-wmf.16/includes/MediaWiki.php(654): MediaWiki::preOutputCommit(RequestContext, Closure) #8 /srv/mediawiki/php-1.37.0-wmf.16/includes/MediaWiki.php(948): MediaWiki->doPreOutputCommit(Closure) #9 /srv/mediawiki/php-1.37.0-wmf.16/includes/MediaWiki.php(559): MediaWiki->main() #10 /srv/mediawiki/php-1.37.0-wmf.16/index.php(53): MediaWiki->run() #11 /srv/mediawiki/php-1.37.0-wmf.16/index.php(46): wfIndexMain() #12 /srv/mediawiki/w/index.php(3): require(string) #13 {main}
In T287780#7251693, @Zabe wrote:I had the same error, but on a second try I was able to create https://test.wikipedia.org/wiki/SecurePoll:828.
In T287780#7251727, @dom_walden wrote:Oh. I tried 4 times in a row (on votewiki) but was not able to :(